Let’s Understand Cloud Computing Security in Detail
Cloud Computing Security is imperative for the smooth operation of businesses today. According to the latest statistics revealed by International Data Group, almost 70 percent of the businesses today resort to Cloud Computing for handling their crucial business data and manage their business processes. Today, vulnerabilities like data security and network security issues lead to grave business losses if not managed correctly through timely intervention. This is where cloud computing security plays an important role in safeguarding the business information and mitigating the major security risks like cyber-attacks, DDoS attacks, and other enterprise bugs.
The important question that needs to be addressed is What are the Key Benefits of Cloud Computing Security?
Once this is determined, it becomes easier to implement the most suitable security measures to the business data networks on clouds.
What is Cloud Computing Security?
Cloud Computing Security is an important feature of a business’ network infrastructure that provides multiple levels of control in order to monitor the system, analyze threats, raise the red flags, trigger warnings and security measures, and provide timely protection in continuity for cloud-based assets like websites, files, network elements, servers, web applications and software.
Whether the business infrastructure is located on a private cloud, public cloud, or a hybrid one, Cloud Computing Security provides the means of balancing DDoS protection, high availability, regulatory measures, and data security initiatives.
Cloud Computing Security Addresses the Following Challenges
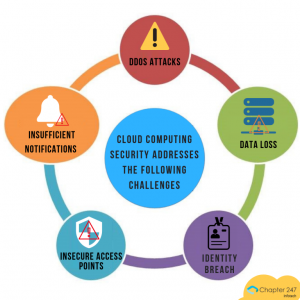
- DDoS Attacks-
The Distributed Denial of Service (DDoS) attack by cyber attackers is prevalent on large networks with huge volumes of data and interfaces that need to be handled by service providers with the SaaS cloud model being the most common target. Vital information on servers can be denied to the authorized users, while the attackers can gain access to sensitive information and misuse it to sabotage a business, like loss of revenues, customer trust, and brand authority. The network gets flooded with requests from fake IP addresses which will increase the turnaround time for a valid request and slow the servers. This could also crash servers making them vulnerable to attackers. - Identity Breach-
Identity theft by hackers is the primary reason for data alterations and breaches according to the Identity Theft Research Center. A rightly designed security system should be in place to address this setback. The right information in the wrong hands can prove to be detrimental to the business. - Data Loss-
The other major aspect of security issues in cloud computing is the loss of vital data which can happen due to unsolicited access to data networks. A lot of interdependent information is stored on servers, which if lost, can lead to recursive data loss, system dysfunction, and disintegration in network functionality.
- Insufficient Notifications and Alerts-
Continuous monitoring and appropriate communication of major breaches are important. Timely alerts to application managers, alarms, and automated backups and corrective actions are essential system functions that will protect business data on a cloud. An ineffective notification and alarm system can make a critical issue go unnoticed and lead to business information sabotage. - Insecure Access Points-
Compromised cloud systems are always susceptible to risks like insecure APIs and network elements. If the access points aren’t secured with appropriate measures, they become vulnerable to attacker exploitation. Improper scanning of network traffic, HTTP requests, acknowledgments, and return values can disrupt the entire cloud network.
cloud computing security needs For Cloud Computing Security
Considering the 5 Key Challenges of Cloud Security delineated above, the need for Cloud Computing Security arises automatically. The need for Cloud Computing Security arises because of the following functionalities which need to be implemented on the Cloud Infrastructure.
- Network Traffic Analysis and routine monitoring of workspaces
- CSP data encryption check
- Multi-level authentication through SMS, security questions, etc.
- Threat type Identification without human Intervention and application of the designated plan of action using a schema
- Automatic switch from central management to local control in case the central server is attacked
- Raising the correct red flags and warnings
- Conducting automatic updates and recovery schedules to always keep the system updated on security implementation
- Taking data backup and storing sensitive data in a secure location
- Restoring important files and data through timely intervention for ensuring smooth system functionality and reducing risks of attacks
- Diligent access points security
- Appropriating user-specific and role-based access management
- Performing network audits and generating security reports for different levels of severity
- Deploying agreed set of rules on servers connected to a client of the same build
- Preventing insecure APIs, cloud service providers’ (CSPs), network elements, and software exploitation that are accessible via distributed access and exposure
- Preventing Malware and Ransomware attacks that can handicap the business network
- Addressing data breaches on the network including the hacking of high-profile enterprise accounts
- Deterring non-compliance issues with the latest security standards that could lead to blacklisting
- Monitoring and preventing internal data misuse that leads to data integrity compromise
- Securing the network from Denial of Service (DoS) and Distributed Denial of Service (DDoS) attacks that freeze servers or slow them down by flooding the network with unsolicited traffic
- Handling data losses due to malicious attacks, natural disasters, or accidental data effacement by the cloud service provider
- Securing vital data from vendor lock-in
- Countering crypto jacking that leads to the mining of cryptocurrency
- Inspection of insecure login sessions
- Handling Advanced Persistent Threats on servers
- Preventing unauthorized access of shared resources on the same cloud between users
You may also like: Future of Cloud Computing in Retail Business
Top Benefits of Cloud Computing Security
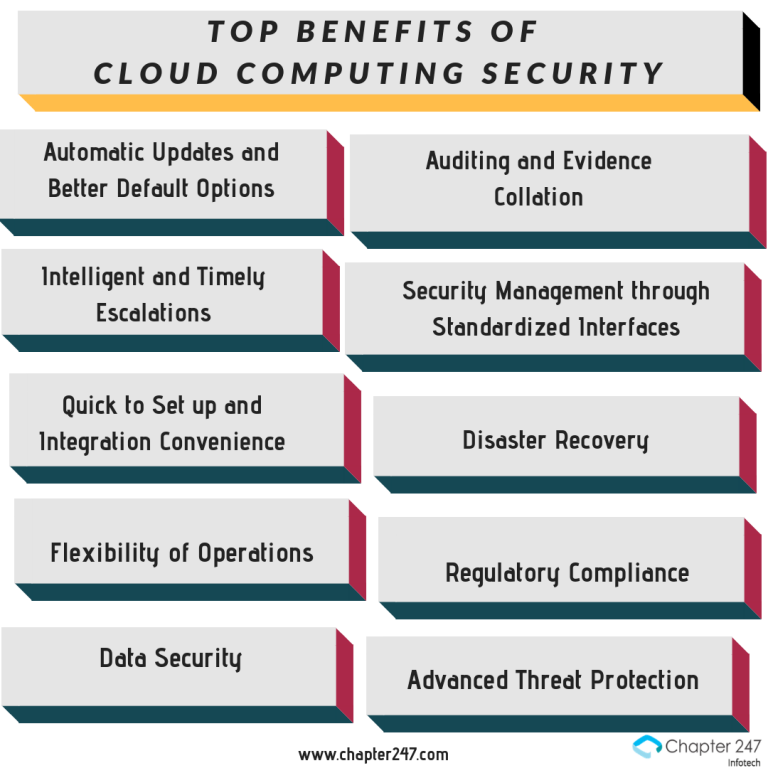
- Automatic Updates and Better Default Options-
Through security features like CMS version and third-party plugin analysis and updates, many cloud security services ensure that software updates take place automatically at regular intervals through the application of the latest patches and security configurations. This helps in managing the risks of cloud computing efficiently. - Auditing and Evidence Collation-
Through virtualization security measures, cloud computing security can provide forensics reports on the usage of various network resources with timestamps for investigations. All the evidence are automatically stored for recording logging activity and other interventions without the performance being affected. - Intelligent and Timely Escalations-
The Security Infrastructure on a Cloud supports automatic and dynamic reassign filters, authentication, failure management, cataloging, encryption, resource allocation, etc. in order to defend cloud vulnerabilities. It helps in the timely management of risks and resisting major pitfalls in network security through escalations. - Security Management through Standardized Interfaces-
Businesses can provide standard user interfaces within their network with enhanced security features with company policy compliance. This uniformity ensures an open security market with standard practices and availability. Also, while integrating with other business applications on the cloud, cross-browser and device-compatibility checks need to be performed by the selected Cloud Security System. - Quick to Set up and Integration Convenience-
Keeping the business infrastructure on a cloud in mind, easy security set up can be done using existing frameworks while concentrating on the elements that need bespoke security features. This saves a lot of time and saves efficiency for other tasks. The security software for any additional network elements can be easily integrated and customized which leads to better network scalability. - Disaster Recovery-
Even though certain advanced risks cannot be prevented on a cloud, disaster recovery can be applied to the affected nodes by updating the lost or corrupt files and addressing dependencies with a good recovery management system. Cloud Security Challenges with respect to data loss, portability issues, vendor lock-in, data explosion, data protection, etc. can be mitigated using the disaster recovery features of cloud security. - The flexibility of Operations-
An Increased scale of security operations ensures authorized access to information from multiple locations and the maintenance of information integrity. The ability to process data flexibly on network elements is an important advantage of Cloud Computing Security. Quick response to security incidents and the prevention of threats is facilitated by scalable security solutions. - Regulatory Compliance-
Different businesses have different governmental and regulatory compliance requirements which have to be met for the business to continue its operations. A robust cloud security infrastructure can provide enhanced support for each of these regulatory requirements while handling security issues. The business information and customer information of the business are rightly protected through this initiative. - Data Security-
Identity management tools, access control, prevention of intrusion, and virus/malware/ransomware protection significantly reduce cloud computing security issues. Security protocols can be implemented to protect the communication between deputed servers. Sensitive information and transactions need to be encrypted using Transport Layer Security and Secure Socket Layer Security. - Advanced Threat Protection-
Advanced threat protection schemes infuse high-fidelity machine learning techniques and detection mechanisms for the most extensive protection against ransomware and other advanced attacks. Reduction of false positives during security inspection with attenuation, statistical analysis, and blacklist checks is performed by installing security monitoring systems.
Choosing the Best Cloud Computing Security Provider for Your Business
Regardless of the type of business that is moving into a cloud computing infrastructure, the organization can greatly benefit from investing in Cloud Computing Security. Depending on the business requirements and the investment capacity, the security solutions enforced on the cloud may vary.
Also Read: Strategic Importance of Cloud Computing in Business Organizations
Here are the factors that different organizations must consider while choosing their Cloud Security Service Provider:
Startup and Newly-Launched Businesses
Startup companies or businesses that are opting for cloud computing infrastructural support for the first time will have lesser data to be managed on the cloud. Thus, the cloud infrastructure and its security environment need to be set up from the rudimentary level. Security for the storage structure and the mechanisms applied on the network elements need to be worked on from scratch. An experienced cloud security provider with flexible security plans and solutions will be an optimal choice.

Investing in an Infrastructure as a Service (IAAS) model is advisable since renting of a readily available data center to host software, services, files, etc. can save costs and provide resource support for your patented solutions. Cloud security providers who offer this model would be an ideal choice.
Small to Medium Scale Business-
If you have a business that has been operating for more than five years, and you are already using cloud computing services, then choosing a security service provider with flexible solutions for existing and new resources is a good move. The service provider must perform the following functionalities

- Improvement in current security features and processes
- Handling of security for data volumes (old and new) that need to be handled, gathered, sorted and processed
- Security based on the current storage infrastructure and new storage capacities that would be included in the future
- Security solutions for the Platform as a Service (PAAS) model which helps businesses design and manage their own solutions on a rented platform
- Basic email security using legitimate servers of inbound and outbound emails to prevent phishing and protect systems from malicious attachments
- Principle data protection on public, private, and hybrid networks
- Basic checks on internal data that is stored in the cloud for compliance with international standards
Experienced Industry Key Players-
Most experienced players in the market have industry experience of more than ten years.
Such enterprises would have separate business domains set up on the cloud for accounting, human resources, operations, etc. The Software as a Service (SAAS) model is used by major corporates to handle their domain-specific operations. High-profile security service providers who handle security as a mainstream activity are preferred to handle the following functionalities:

- Advance compliance checks with security standards like CIS, ISO, NIST, HIPAA etc.
- End-to-end encryption management including decryption, hashing, digital signatures, key exchange, and certificate generation and renewal
- Maintenance of data exclusivity through user-specific content disclosure, process validation, process management, and secure login services
- Fulfillment of API security requirements for different environments on cloud communication solutions
- Automatic behavior monitoring and isolation of suspicious activities through machine learning
- Real-time URL and IP address analysis for identifying vehicles delivering ransomware and IP spoofing
- Digital signature feature programming for emails and files to enable identification and non-repudiation
- Intrusion management using pattern recognition to detect and handle unusual events
- Advanced perimeter firewall set up for granular packet integrity inspections (source and destination packets)
- Development of internal and external Intrusion Detection Systems with Event Logging Support
- Contingency reporting system development for advanced levels of security incident scrutiny
Why Chapter247 Infotech is the Best Cloud Security Service Provider for Your Business?
Chapter247 Infotech has been instrumental in providing a gamut of Cloud Security Solutions to existing and new business systems through its products and services suite, by providing different subscription packages that are based on different budgets and product features listed below;

- Automatic Malware Scan and Removal-
We extensively perform in-depth automatic scans in regular intervals on programs, operating systems, network files, emails, and cloud content for malware like Trojan Horse, Adware, Worms, Spyware, Malware code snippets, Bolts, and Spiders and removes them using the latest code patches and annihilation of backdoors, rootkits, and Trojan horses. - Blacklist Monitoring and Removal-
Blacklisting of non-compliant or suspicious email IDs, IP addresses, Cloud elements, observation, detection, and correction of network downtime is done on the cloud infrastructure using this service. Removal of suspicious accounts and information is done by eradicating risky websites, virtual server hardening, software quarantine etc. - Scan and Block Hacking Attempts-
This service includes the following:- FTP access limitations
- Dynamic blocking of multiple login attempts
- Entry points access control
- Software scanning program(s) installation
- Removal of faulty or suspicious information
- Firewall configuration issues
- Automated Website Backup-
Software services that automatically creates and updates backup files for dynamic websites and their databases are created by Chapter247 to counter the risks of Cloud Computing like data corruption or deletion while assisting in the shielding of sensitive information.
The cloud elements that benefit from this service are:- Website files
- MySQL database files
- Images and content
- Scripts and applications on the website
- cPanel email forwarding structure and stored email
- Security Integration with Applications-
This service provides prompt protection against web application security risks, SQL injection, cross-site scripting, illegal resource access, unsolicited remote file inclusions, and targeted information vulnerabilities. - DDoS Protection-
This service secures all cloud elements and resources from intruder attacks and Distributed Denial of Service issues. Identity and access management mechanisms applied include cloud identity, generating security keys, cloud resource manager control, and other identity solutions.
Conclusion
Cloud Computing Security measures are paramount in any modern-day enterprise for ideal functioning. Challenges in reliability, cost, and efficiency need to be handled through the accurate implementation of effective security footprints. For the best Cloud Security Solutions get in touch with us today.
You are just a call away to Secure your Business system with our Cloud Computing Security Expert. Call us today and get the best Cloud Security Consultation for your organization.
Contact us at +919009077766 or drop a mail at askus@chapter247.com.







